Since the beginning of this year, organizations have been under increased pressure to provide quick and effective ways to allow employees to effectively shift from working in the office to working at home. Many organizations had to scramble to provision infrastructure and technologies that allow employees to remotely connect to business-critical resources. 
While some businesses may have adopted new and modern technologies for empowering employees for remote work, others may have leaned on technologies that have existed for decades now. One such technology is the virtual private network (VPN).
VPNs have been a staple in most enterprise organizations and do allow remote employees to connect to internal resources. However, VPN is quickly showing its age in a number of key areas that your business needs to consider. These include security, performance, scalability, and simplicity. Let’s take a look at these and see how you can move beyond the VPN for your business and the path you can take to get there.
What is a Virtual Private Network (VPN)?
Let’s begin by taking a step back and consider what a virtual private network (VPN) is and see how it has enabled remote work for years now. The virtual private network (VPN) is a longstanding technology that has enabled enterprises to effectively A) connect remote networks together, and B) enable remote clients to be able to connect to internal corporate resources. This can be achieved even if the end user is located on an untrusted network.
Using a VPN connection, the corporate network can essentially be extended to the remote end user so that data can be sent and received as if the end user was located inside the corporate network. VPNs work by creating a securely encrypted tunnel between end users and a corporate network or between two different trusted corporate networks. This is a common practice to connect remote office networks to the corporate network.
The encrypted tunnel is established using a layered tunneling protocol and various encryption technologies. The following are common VPN protocols for securing data:
- Internet Protocol Security (IPsec)
- Transport Layer Security (TLS)
- Secure Socket Layer (SSL)
In the case of a remote worker, this means even if the end user is located on an insecure network across the Internet, the VPN connection can be established and the encrypted tunnel allows the end user to “become” part of the corporate network without the possibility of someone snooping on the network traffic in between the client and the corporate network. This allows remote clients to make use of public Internet locations such as public Wi-Fi hotspots to access corporate resources with the tunnel back to the office being encrypted.
While there are many different flavors of VPNs, in the case of an end user client, they generally allow the client device to be presented on the corporate network as it would if you simply patched the device into a switch located on-premises. This allows providing a way for an end user working remotely to be able to launch and use applications that require internal resources that are only available on the internal corporate network.
These types of resources may include intranets, internal databases, and other business-critical application servers that are not forward-facing. Using a VPN connection allows the remote client device to be presented on the same IP address space of internal corporate resources or an adjacent space that is internally routed to the other internal resources. Again, this allows the same behavior as a client who connects to the physical network into a “client” VLAN that has a route to internal subnets containing server resources.
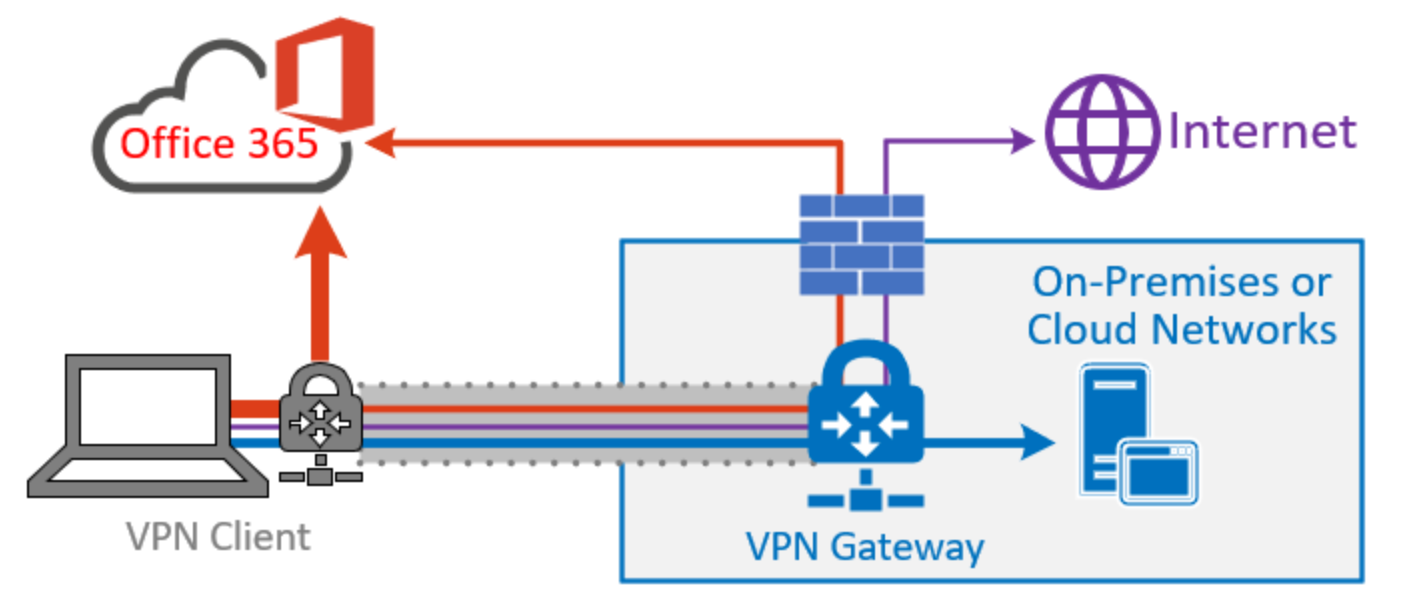
High-level overview of a common VPN (image courtesy of Microsoft)
Since VPN technologies are tried and tested for many years and have served enterprises well for decades, why should your business move beyond the VPN for providing connectivity to end user clients?
Why should your organizations move beyond VPN?
There are a number of reasons that organizations today should be looking to move beyond the confines of VPN connections for remote end users. Let’s focus on the following reasons and see how VPNs limit your organization in each of these categories:
- Security
- Performance
- Scalability
- Simplicity
Security
Today, security is most likely leading the list of concerns your organization has in terms of architecting infrastructure solutions. With major data breaches, ransomware, and other security risks, organizations everywhere are having to reevaluate the tools, solutions, and architecture of all aspects of business-critical systems. This includes remote access.
The VPN solution was designed for the security problems companies were facing 20 years ago, where many of today’s threats had not yet appeared on the scene. While VPN allows securing the tunnel of communication between the end user client and the corporate network, it doesn’t account for the fact that you are placing the end user client on an entire internal corporate network subnet along with other corporate devices.
Today’s security models recommend a zero-trust stance for all devices connected to the network. This means that it is no longer feasible to simply trust a VPN client to connect to your network with carte blanche access. All network endpoints, including those on-premises, should have access to only those resources they absolutely need to communicate with. This model does not fit well with traditional VPN technologies.
Additionally, your organization’s data is the most valuable asset and resource that you have. End user clients that use VPN often hold the data on the actual end user device. This could be a laptop, desktop, or other mobile device. Housing data outside of the corporate datacenter is dangerous. This means that an attacker who compromises a client device now potentially has access to sensitive business data.
VPNs also easily allow for the exfiltration of data from the corporate network. An unscrupulous employee can easily copy data from a VPN-enabled client to a local storage device or even personal cloud storage. This opens your business up to all kinds of risks, including data leak and compliance violations.
This is certainly not desirable. Data breach costs are staggering. With the newly released report from IBM Cost of a Data Breach 2020, take note of the following statistics:
- Average cost of a breach worldwide – $3.86 million
- Highest cost industry – Healthcare, $7.13 million
- Highest cost country – United States, $8.64 million
- Impact of COVID-19 – 76% of companies said it would lengthen the time needed to respond to a data breach
While VPNs allow remote connectivity and secure the connection in between client/corporate, they do not protect your data. Additionally, malware, ransomware, and other malicious software variants can easily infect corporate networks by way of connected VPN clients.
Most remote workers just need access to the business-critical applications they need to stay productive. This means that connecting a full end user client to the network is certainly “overkill” to enable business productivity. To move away from VPN technologies for remote workers, focus on remote connectivity solutions that allow application connectivity and not full network access.
Performance
VPNs are not known for their performance. Rather, most end users are more familiar with VPN performance issues. Organizations generally run VPNs from firewall devices or they may actually have VPN concentrators that aggregate VPN connections.
However, there are many factors that can lead to VPN performance issues including:
- Overloaded VPN servers/devices
- Poor Internet connectivity between VPN client and corporate
- Lack of scalable VPN solutions
All of the above can lead to a VPN experience for end users that impedes productivity instead of enhancing it. This can also increase the support burden on help desk technicians and network engineers who may already be spread thin since the start of work-from-home initiatives introduced earlier this year.
Scalability
The requirements of the modern workforce have evolved and “outgrown” the capabilities of VPN technologies. End users working remotely need to have unfettered mobility, the use of digital workspaces, and access to cloud data and services.
This has led to most businesses looking at a “cloud transformation” to solve many of the issues of on-premises infrastructure. When you start looking at the requirement to launch and connect VPN clients across all devices and possible scenarios to allow remote workers to have access to all the applications and data they need, this can become extremely complex and inefficient, very quickly.
For your organization to effectively support the needs of remote workers today as well as future needs that may arise tomorrow, leveraging a cloud-driven framework for application access is the smart move to make. Standing up a digital workspace with an underlying cloud architecture allows these capabilities.
Cloud has driven the digital workspace initiatives of most businesses. Digital workspaces allow for:
- Dynamically scaling up & down based on user demand
- Lower support costs
- Agility in operations for your business
Simplicity
When supporting remote workers, simplicity is key. Complex and overly complicated requirements for end users to connect and run applications via VPNs means much higher support time and costs for each remote employee. Configuring, setting up, and troubleshooting VPN connections can be a tremendous burden on your organization.
Choosing a digital workspace solution that allows connecting and running applications without the need for VPN is a much simpler and easier process for end user employees. Modern digital workspace solutions allow accessing applications and interacting with business-critical data via a simple browser session!
Cloud-Native Digital Workspace Technology
Does VPN still have a place? Yes, it certainly can. VPN connections are still beneficial for site-to-site connectivity in many cases and can provide an alternative way for network management and other functions as needed. However, for empowering today’s remote employees to be productive and access applications and data, not so much.
Making use of an application-centric digital workspace technology, like Cameyo, allows your business to have the performance, scalability, and agility needed to power productivity, without complexity. Focusing on applications enables you to eliminate the underlying requirements of VPNs, lowering your support costs.
Using a digital workspace to provide access to all the applications and services that remote employees need through a standard SSL-encrypted web browser allows accessing apps across any device and from any location with only an Internet connection.
This is the flexibility and mobility needed by your employees. It can be achieved by moving past VPNs and deploying digital workspace technologies to deliver the tools your remote workers need to be highly productive.
