According to Statista, 68.5% of businesses have been victimized by ransomware in 2021. The highest percentage reported to date. And as companies move to a hybrid work environment, workers will continue to access business-critical applications remotely. This is why it’s now more critical than ever to understand and address how legacy remote desktop and virtual desktop technologies impact the security of your remote & hybrid workforce.
In the wake of the recent Kaseya ransomware attack, there is now an increased level of scrutiny. But most Virtual Desktop Infrastructure (VDI) and Desktop as a Service (DaaS) products do not provide adequate protection against ransomware and other remote access security threats. In addition, organizations relying on Remote Desktop Protocol (RDP) – the proprietary Microsoft protocol that enables remote connections to other computers, typically over TCP port number 3389 – that require open server ports to the Internet are at even greater risk from brute force and RDP-specific attacks like BlueKeep.
[NOTE: If you’re looking for more info on how to configure your remote desktop connection and new RDP ports/RDP port numbers, how to utilize registry editor/regedit, terminal server, configuring port forwarding, UDP ports, a new port number, standard port, localport, custom port and the listening port, etc., you can find some Microsoft resources here, and a great WikiHow resource here. Also, see the end of this post for more detailed information from our Knowledge Base about diagnosing RDP port issues.]
To increase security, VDI, DaaS, and RDP companies typically recommend adding VPNs, using strong passwords, implementing two-factor authentication, performing regular software updates, using a remote desktop gateway, installing the latest OS patches, enforcing account lockout, and implementing a centralized audit trail. With advice like this, it’s a wonder the number of ransomware victims isn’t 100%.
Understanding the Attack Vectors
According to Coveware’s Quarterly Ransomware Report, “in Q1 (2021) compromised remote desktop protocol connections regained the top position as the most common attack vector. RDP remains a frustratingly common vulnerability despite well known secure remote connection best practices.” See the chart below to see how RDP overtook email phishing as the leading attack vector in Q1:
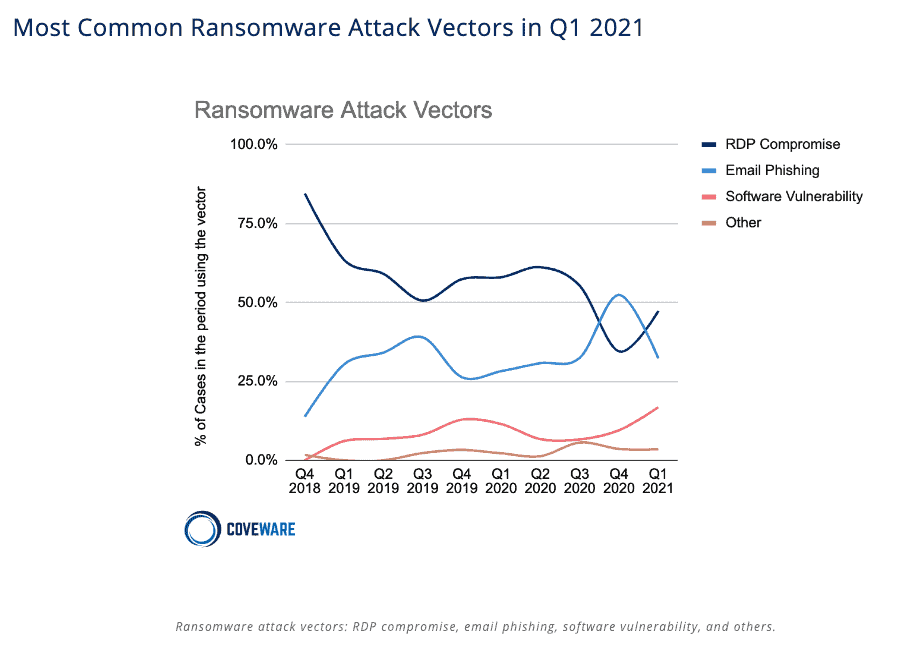
Moreover, the larger an organization gets, the bigger problem RDP becomes. For companies over 10,000 people, RDP was the attack vector for over 50% of ransomware attacks. That number increases to nearly 75% as organization size grows to 100,000+ people.
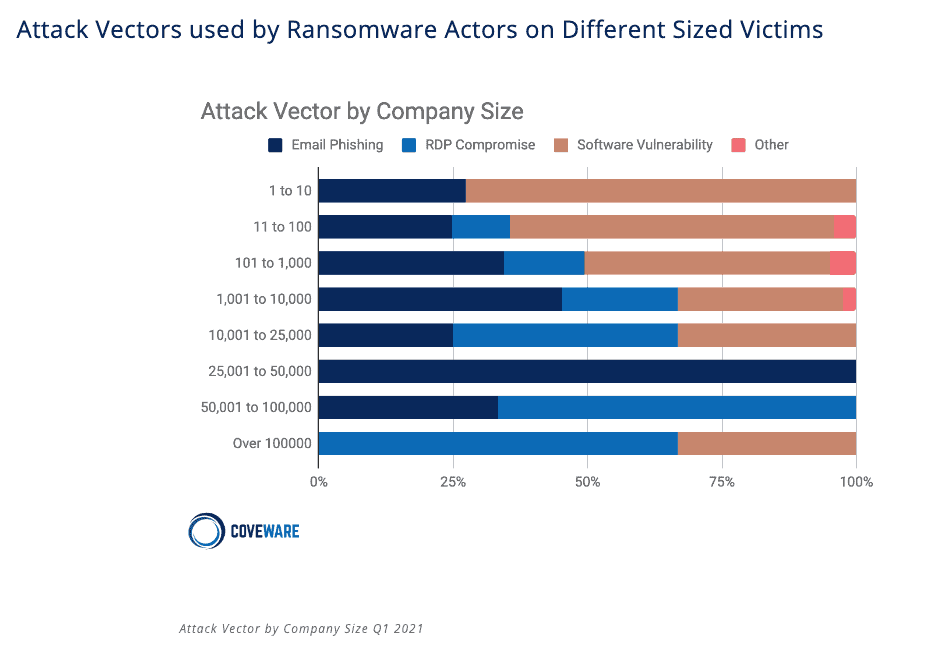
Why the Rise in RDP Attacks?
One could safely assume that the dramatic spike in RDP being used as an attack vector directly correlates to the rise in remote work brought on by the pandemic. That’s true, but it’s not the whole story. Back in 2019 the McAfee Labs Threat Report reported that ransomware and brute-force attacks increased by 118% that year – and that much of that access was gained by brute-force attacks to open and exposed remote access points such as RDP. So this trend began before the pandemic, and was then accelerated by it.
But let’s take a step back – what do we mean when we talk about open/exposed RPP ports?
When organizations configure and enable remote functionality on a Windows server, they open its RDP ports to the outside world, specifically ports 3389, 3387, 3392. At that point, if the server is connected to the Internet, it is vulnerable to RDP brute-force attacks. While opening RDP ports to the Internet was uncommon a few years ago, it has unfortunately become the de-facto standard when creating cloud Windows instances.
But What Do These RDP Attacks Look Like, Really?
Back in September of 2019 our own Cameyo research showed that the average internet-connected server faced 150K brute force-triggered password attempts per week, performed by automated bots, scripts, viruses and zombie machines. We began using our RDPmon solution to monitor our own environment and in less than 6 months, Cameyo’s RDPmon recorded 7 million RDP password attempts on our ‘honeypot’ server. That means that the average number of brute-force triggered password attempts was over 318K attempts per week – and that was BEFORE the pandemic moved the world to remote work.
And in reality, that’s just the beginning. The increase in RDP-focused attacks are exponential. At first, only a few bots attempt to connect every few hours, and then as soon as they detect your RDP port as being exposed, they make more and more attempts, resulting in an exponential increase over time.
This is part of the reason we introduced Cameyo Port Shield back in 2019. Port Shield is the first security solution capable of automatically and dynamically opening and closing RDP ports on-the-fly at the Windows Firewall level, rather than statically. Unlike other solutions that keep RDP ports open only to a pre-defined number of IPs – thereby limiting cloud and geographic flexibility – Cameyo proactively closes the RDP port at the Windows Firewall and only opens it if/when needed based on a validated user’s IP, authenticated through Cameyo’s central portal.
And the best part? Cameyo Port Shield is completely free for all Cameyo customers. Because at Cameyo we view security as foundational, never something that should be “optinoal”, there is no action required to utilize this feature – it is active for all users of the Cameyo platform, and is included at no additional cost.
And Port Shield is just the beginning of our end-to-end, Zero Trust security approach. Cameyo Virtual Application Delivery platform was designed since day one to be the simplest and most secure way to deliver business-critical applications to users in a hybrid and remote work environment. Cameyo’s single architecture and Zero Trust security model includes:
- Limited attack surface – Cameyo’s single architecture eliminates the need for additional gateways and appliances that can fail and become a security issue on their own (e.g., CVE-2019-19781 – Vulnerability in Citrix Application Delivery Controller, Citrix Gateway, and Citrix SD-WAN WANOP appliance).
- Port Shield – a Cameyo-developed technology provides built-in security that automatically closes RDP, HTTP, and HTTPS ports and opens them to authenticated users only when needed.
- No VPN – all traffic is encrypted and apps are delivered from a secure HTML5 browser, effectively separating the user’s device from the corporate network and eliminating the need for VPNs.
- Non-persistent servers – customer user data is removed from the Cameyo server every time the user logs out, and in the very unlikely event that the secure browser is penetrated, the hacker only has access to the user’s session and is wiped from the server when the session ends.
We’d love to schedule a demo and show you first-hand how Cameyo’s ultra-secure Virtual App Delivery platform can help protect your organization from ransomware, including the growing issues of RDP vulnerability as the primary attack vector. You can schedule a demo here, or contact us at sales@cameyo.com anytime to set up a demo. Want to test drive it yourself first? Start your free trial (no credit card required) here within minutes.
Diagnosing RDP connectivity issues
For additional information on configuring RDP in Windows 10, Windows 7, and other versions of Windows environments, the following from the Cameyo Knowledge Base (view full article here) talks about collecting advanced information about RDP connectivity issues from Windows’ Event Viewer.
This article deals with advanced logs pertaining to connectivity issues. In other words, sessions that fail to start Cameyo during the “Connecting” phase. This article does not deal with problems pertaining to the “Provisioning” phase or issues during an ongoing Cameyo session.
Windows contains a lot of information and tools for diagnosing RDP issues. They are centralized in the event viewer. Hence, start by logging into the relevant server as an admin, and open the event viewer (eventvwr.msc). There, you’ll need the time to see whether the connection has reached Cameyo’s server-side guacamole module, search the Windows Logs\Application log for errors with source=guacd. Look at the Details | XML tab. In the below example, guacd is complaining about an error connecting to the RDP server on that same machine:
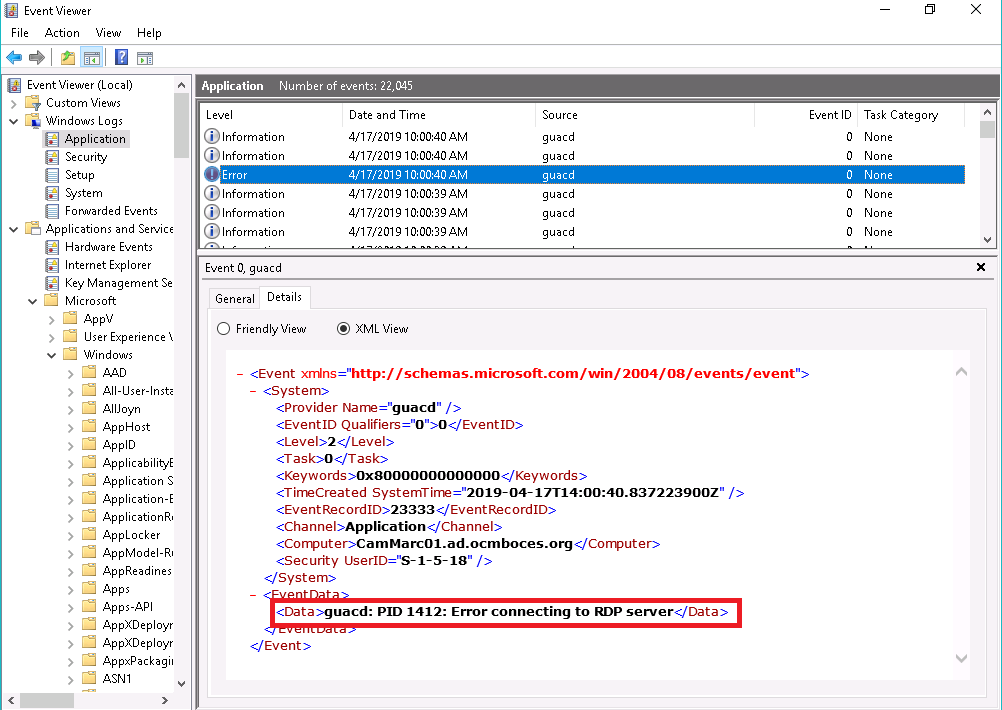
From there, you want to check whether the login was accepted. Sometimes (although rarely) logins can be refused due to invalid credentials, expired user accounts etc. In the below example, RemoteUser1’s login was successful at 9:07:45am but immediately followed by a logoff event:
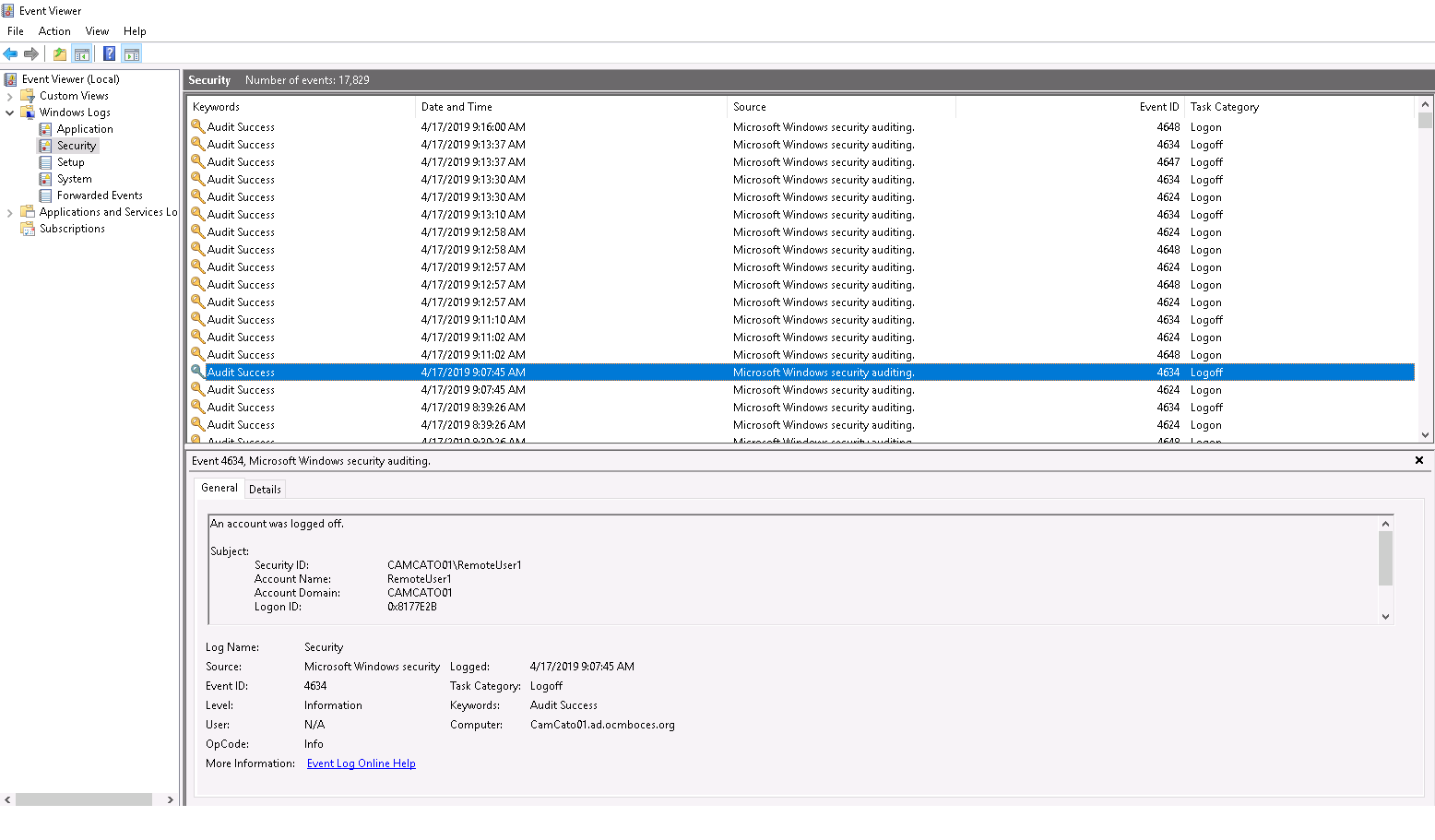
Now it’s time to dig into another, more advanced log: the Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational log (under Applications and Services\Microsoft\Windows\RemoteDesktopServices-RdpCoreTS\Operational):
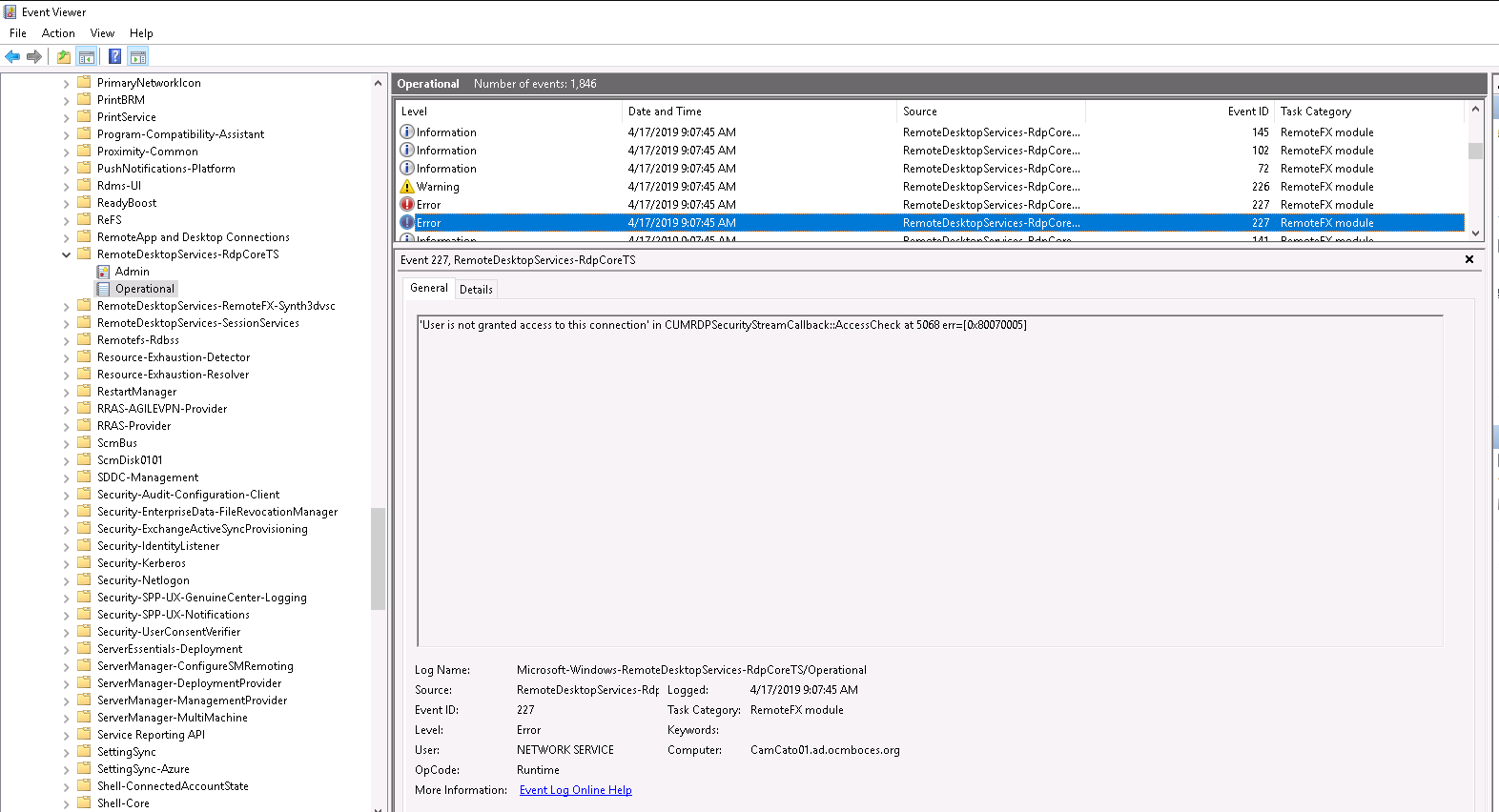
At the time of the connection issue (9:07:45am) you can see an error “User is not granted access to this connection […]”, thus a policy issue.
In this specific case it was due to the user not being part of the “Remote Desktop Users” group. But this is just an example. Note that this works for remote computer/remote desktop clients and on various operating systems including Windows Server 2003, Windows Server 2008, Windows Server 2012, Windows Server 2016, and above.
