There is no question about it, the past few months have certainly made organizations rethink the layout of their workforce. At the first of the year, no one could have seen a global pandemic coming. However, business had to react to the situation at hand, quickly and decisively. 
Due to the suddenness of how the global pandemic has unfolded since the beginning of the year, many organizations had to simply get a solution in place that could allow employees to connect via remote means to business-critical resources. Unfortunately, for many, this may have involved foregoing many security best practices to simply allow business-critical operations to carry on.
Now that we are months into the pandemic at this point, many organizations are rethinking the security of remote solutions since the current remote-centric workforce may be the path forward as part of the “new normal” of today’s work environment.
Why is remote security so important? What is at risk for your business? Let’s consider how to maintain security when employees work remotely and outline specific best practices for doing so.
Why remote security is so important
When it comes to your organization’s data, it must be protected at all costs. We live in a world where attackers take advantage of any possible security vulnerability, distraction, or disruption that can lead to compromise. This includes the current COVID-19 pandemic.
Attackers have already shown a willingness to use the current COVID-19 pandemic to entice and lure end users in with various phishing emails with proposed Coronavirus advice or other medical information. Not long ago, attackers used a real Coronavirus map from John’s Hopkins University to spread malware. These malicious attacks are targeting remote end users.
Why are current remote users a target? As we know, the world is focused on COVID-19. This includes your organization’s remote workers. Your remote employees are most likely now working from home, which means they’re often facing the distractions that come with working at home with family and other activities around them.
Environments where employees are distracted are much more conducive to end user compromise. Employees may be much more likely to click links in phishing emails or visit risky websites when in the comforts of home or distracted by their environment. This furthers the recipe for compromise in favor of an attacker.
Due to the suddenness of provisioning a remote work solution, many organizations have allowed employees to use their own BYOD equipment to access remote work environments. Personal hardware and software environments for individual employees may house potentially unwanted programs (PUPs) and other risky software that may expose your data if not properly secured. This too has potentially lowered the bar for the overall cybersecurity of remote employees.
The actual remote work infrastructure solution itself may have had to be provisioned hastily. In many cases, this has been done without proper security in mind just to maintain business-continuity. This leads to many environments now being “ripe for attack” across the board.
We know that attackers have their sights set on businesses. An alarming trend when looking at recent ransomware attacks is attackers are heavily targeting businesses across the board. Ransomware detections among businesses from 2018-2019 rose by 363%. Just recently, the Evil Corp hacking group targeted some 31 companies seeking to deploy ransomware called WastedLocker. As evidenced, this is certainly a trend that continues amid the pandemic and remote work situation.
When we look at the danger that is posed not only to the end user but also to your organization as a whole from remote worker compromise, the security ramifications can be catastrophic.
What is at stake?
Let’s take a step back and understand what is at stake when thinking about proper remote security. What can a data breach cost your organization? The IBM 2019 Cost of a Data Breach report helps to underscore the importance of minimizing the risk of a cybersecurity breach of your environment.
Note the following alarming statistics that pertain to a data breach:
- Highest cost of data breach (Country: U.S.) – $8.19 million
- Highest industry average cost (Healthcare) – $6.45 million
- Average time to identify and contain a breach – 279 days
- Average size of a data breach – 25,575 records
- Average cost per record for a data breach – $150
Aside from the fiscal implications that a data breach entails, your organization can suffer untold long-term damage from loss of customer confidence and trust. The fallout from a data breach can impact your business for years. About one-third of data breach costs occurred more than one year after a data breach incident.
How to maintain security when employees work remotely
Remote security under the “new normal” is more important than ever before. It requires that businesses do their due diligence to ensure that solutions used for remote productivity are secured in a manner that minimizes cybersecurity risks.
Let’s take a look at the following remote security best practices and see how these can minimize the cybersecurity risks to your organization’s business-critical data:
- Educate your end users
- Control where data is housed
- Encrypt data both at-rest and in-flight
- Double down on email security
- Use Multi-factor authentication
- Use application virtualization instead of infrastructure virtualization
1) Educate your end users
End user cybersecurity education is essential for helping end users to take ownership of their overall security and empowering them to make good decisions to protect themselves and the business. General cybersecurity education for end users may involve the following:
- Helping users understand what a phishing email looks like
- How to verify the sender of an email is who they say they are
- Questions to ask when certain types of information are requested by a sender
- How to scrutinize embedded links, software installation prompts, and permissions requests in the case of cloud applications.
- What precautions to take when browsing the Internet
These are only a few of the items that a basic cybersecurity training course can help with. Many resources allow cybersecurity training to be carried out remotely or online which is extremely beneficial given the current circumstances. The rewards of basic cybersecurity training can be immensely beneficial.
2) Control where data is housed
Organizations may currently use remote technologies that allow end user devices to “become” part of the corporate network. Technologies such as VPN allow this type of connectivity for end user devices. The problem with VPNs and technologies like them is they can allow data to traverse from the boundaries of your corporate data center to an end user device.
As alluded to above, there are all kinds of reasons you do not want this to happen. This means that potentially sensitive data can find its way onto an end user device. Additionally, any attacker who may compromise the device of a remote worker will have gained access to the “inside” of your network by means of the VPN tunnel established between the remote device and the corporate network.
It is essential in the remote solution you employ that you have the means to keep data inside the corporate network and control/prevent it leaving the confines of sanctioned use. Data leaving your environment is a recipe for disaster and can quickly lead to a data leak event.
3) Encrypt data both at-rest and in-flight
Data encryption in the realm of ransomware can certainly be disastrous. However, when you as the business are in control, data encryption is a cybersecurity best practice when it comes to the security of your data.
Data encryption at-rest involves encrypting data that is stored on local storage. Encryption in-flight encrypts data that is traversing across the network. Both are vitally important aspects of remote worker security as both types of encryption help to ensure that any data either stored or transmitted is done so in a way that cannot be intercepted and read at any point in the process.
4) Double down on email security
Email has been a staple of business communications for decades. Even with other instant communications tools that are used by businesses today, email continues to be the primary means for business communications across the board. This certainly includes remote employees.
Giving attention to email security is a great way to ensure that cybersecurity threats such as phishing attacks posed via email are greatly reduced. Attackers widely use phishing emails and other communications via email to lure remote workers to install malware or click malicious links.
Implementing strong SPAM and phishing filters as well as disallowing dangerous file types as attachments can go a long way to help bolster the security of your email solution.
Using strong SPAM and Phishing filters helps to reduce cybersecurity risks for remote employees
5) Use multi-factor authentication
Passwords are often a weak point of end user security. Even with password policies and other safeguards in place, end users generally find ways to weaken their account passwords by using common patterns or simple variations of the same password that slide by password policy requirements.
By requiring multi-factor authentication, commonly in the form of two-factor authentication, employees have to prove their identity by using something they know (their password) in combination with something they have in their possession of (their mobile device).
Once the correct password has been entered, the authentication process is still not successful unless the second part of the process is validated. This is often done with a one-time password texted to the end user or by using multi-factor apps that make this process easier (Microsoft Authenticator, Google Authentication, and others).
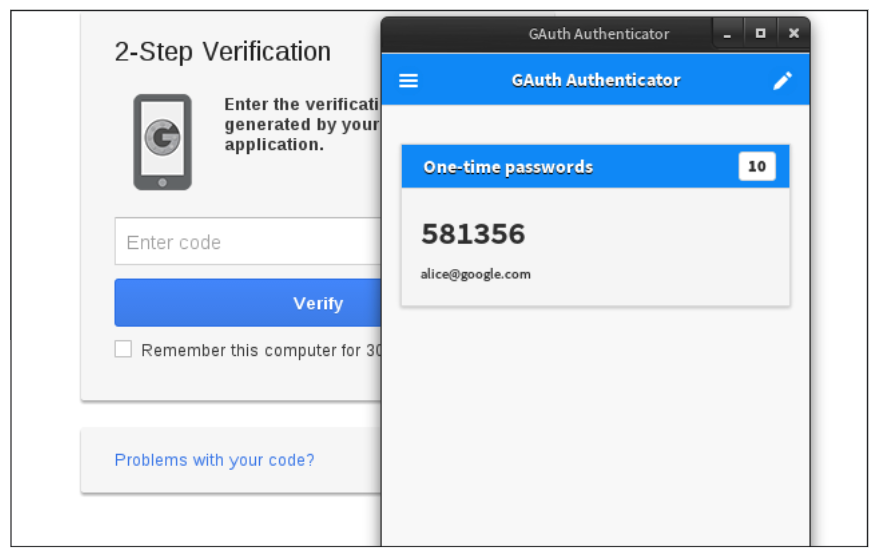
Google Authenticator makes two-factor authentication easier for end users
Multi-factor authentication makes it exponentially more difficult for an attacker to compromise an account since simply having the correct password is not enough for a successful authentication.
6) Use application virtualization and not virtualized infrastructure
There are many virtualization solutions on the market that organizations use today to successfully enable remote access. Most solutions available for enabling remote access do so by virtualizing infrastructure for the remote employee such as the very popular virtual desktop infrastructure (VDI) provided by various vendors.
While VDI and other Desktop-as-a-Service (DaaS) solutions available on the market can certainly enable remote workers to have access to resources, many of these solutions are very complex to configure and manage. They can also be very expensive. Additionally, the complexity often leads to security issues quickly creeping into the environment due to misconfiguration or incomplete configuration.
When it comes down to end users working remotely, most need access to applications, not infrastructure. Application virtualization allows presenting your remote workers with access to the applications they need. This bypasses overly complicated or unnecessary infrastructure components that simply widen the attack surface.
As an example, organizations may stand up the ever-popular Remote Desktop Session Host (RDSH) in the DMZ so that employees can run a business-critical application for accounts payable. Often, this is configured in a way that exposes the extremely vulnerable RDP protocol port to the outside world.
When it comes down to it, the employees simply need to run the accounts payable application. However, to provide access to the application, the desktop is virtualized and exposed to the outside world. When you think about it, this is extremely inefficient and when misconfigured as frequently happens, it is very insecure.
Choosing a remote work solution that enables you to virtualize your applications provides a much more efficient solution in terms of resources and is much more secure as well. The attack surface is greatly minimized with much fewer “moving parts” involved and exposed.
Final Thoughts
With the current remote work situation looking to be the “new normal” for quite some time to come or potentially for the foreseeable future, organizations must take steps to maintain security when employees work remotely. The stakes are high and the risks have never been greater for your business.
Understanding those risks and implementing remote work best practices helps to drastically reduce the risks to your end users and business-critical data. These involve the basics such as training your end users, implementing good safeguards for email and other digital communications, and using application virtualization to deliver what your remote employees need most – secure and efficient access to their applications.
